Cybersecurity: How Marinas Can Keep Business and Customer Information Safe
Published on March 23, 2022The recent invasion of Ukraine and the uptick in cybersecurity warnings put a finer point on what cybersecurity experts have lost sleep over for some time now. Marina customers’ most sensitive and personal information, such as their address and credit card information, is at risk every time a transaction occurs at the marina. How can you keep it safe?
High-Tech Protection
Cybersecurity vendors are constantly working to improve and update products that protect information in the cloud. And marina owners, operators, and staff get peace of mind when they install a platform they can trust, according to Travis Townes, general manager of Twin Creeks, a marina and RV resort on Tims Ford Lake in Winchester, Tennessee, with newly added boutique waterfront cottages. Townes handles some of the facility’s IT operations. While Townes speaks knowledgeably about software integration, he comes from a humble Twin Creeks past. “In 2018, when we opened up our boat rental process, it was actually paper and pen, a binder with 365 sheets of paper in it,” he said.

The company’s rise in cybersecurity came in stages: In 2019 he integrated a different platform for boat rentals. In 2020, when the RV park came online, it was brought onto another platform. But it was inefficient to have two separate reservation platforms that both connected differently with the Twin Creeks website. And it was also difficult training staff on two different platforms. Training is often a big issue in the marina industry, where staff is usually seasonal and transient.
In the spring of 2021, they integrated the marina, boat and property rentals into RMS, a hospitality cloud-based reservation and property management system. This meant Townes and the staff only had to be fluent in one platform. And customers didn’t have to pull out their credit card and identification, for instance, when they had originally rented a vacation unit but now wanted to add a boat rental to the tab. RMS makes it possible to add purchases without resubmitting payment information.
Tom McMahon, RMS senior application manager, said one of the key cybersecurity features of RMS is that it can connect marinas to an active directory, technology that allows the marina to control who can access their data (from a users’ perspective). Often this is used when it is a large enterprise, with many staff members. Standard RMS offerings in this regard entail creating usernames and passwords. Marinas can control it themselves, outside of RMS, in an external database. And the RMS software can integrate with other active directories.
In addition to requiring sign in names and passwords, McMahon said the RMS platform can also provide IP restrictions that can restrict access by range or by country. So, for instance, if you know all your employees are in the U.S., using RMS you can set a limit so that only those people in the United States or with an IP in the U.S. can log into the system, even if they have a valid username.
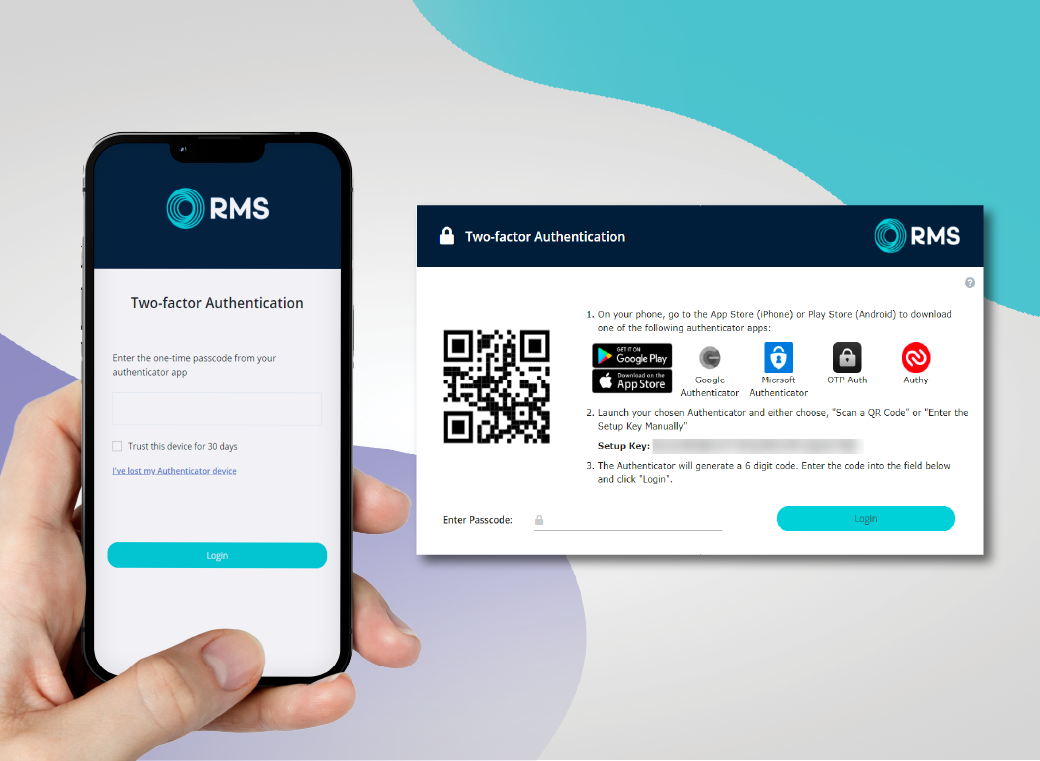
RMS builds two-factor authorization, also referred to as 2FA, into the system, providing another layer of security to online accounts. An additional login credential, such as a randomly generated number code sent to your phone or email, is needed to gain access. “So, it’s a double check to know that it’s a particular user logging into a database, that they are actually employees of the corporation,” McMahon said.
RMS also offers a single sign on, so if the company has a type of intranet, users can sign into it via the company’s directory, versus signing into RMS. The company can have extra protection and firewalls there. They also tokenize credit card information, which replaces credit card numbers with a string of meaningless numbers and letters that are useless to potential hackers. The tokens are then passed through the ‘gateways’ needed to process the payment without the actual bank details being exposed. Rebekah Meadows, corporate sales manager at Twin Creeks, said that when she accesses an existing client’s credit card information, she can only see the last four digits.
McMahon said the tokens, not the credit card information, are stored on their system. He explained that they have integrations with gateways across every county in which they operate.
Protecting Your Investment
RMS Chief Revenue Officer Frederic Dominioni said it is important for business owners to be concerned about security and privacy issues. He added that finding the right technology partner is key to reducing cybersecurity problems. “Many business owners buy 25 different pieces of software then need to train their staff and somehow bridge all the gaps to meet their business goals,” he said. “We aim to streamline that process so businesses can focus on their property and the guest experience.”
Marina owners and operators, like others in hospitality, are typically heads down into their day-to-day operations, and there is often a lack of prescriptive business intelligence to help them understand their business better. In addition to utilizing a platform like RMS, Townes offered a series of tips marina owners and managers should incorporate into their operating procedures:
- Have separate networks for public and office use.
- Consider changing your Wi-Fi password every month or so.
- Never put a guest network on your main network.
- Hardwire all computers to your private network’s router or wireless access point.
- Consider a backup cellular payment processing device in case Wi-Fi goes out. Cellular is less secure, but it ensures that you don’t have to completely shut down and stop accepting payments in the case of a Wi-Fi outage.
- Have all crucial hardware connected to back up batteries that protect it from lightning strikes or power surges.
- Run weekly backups on a disc if you use the cloud to store data.
“It really comes down to your sharing settings on your devices and wherever you store confidential data, whether it be a server for your QuickBooks files or just a restaurant POS system,” Townes added. “Always reach out to a private security firm, even if you are not on a cloud-based data storage platform.”
Cybersecurity Checklist
Tom McMahan with RMS suggested these important policies regarding data protection:
- Protect your database by choosing a complex password that is unique and contains 10+ characters. Store this in a secure password manager.
- Add an extra layer of defense by enabling two-factor authentication. This additional step will ask you to confirm your identify via your trusted device.
- Regularly review users on shared databases and check your system access reports to confirm all recent logins are from genuine users that you recognize.
- Complete cybersecurity training and offer it to employees. Alternatively, there are free online courses available to refresh your knowledge.
- Identify, report, and block any scam or phishing emails. Review domains and do not click on any suspicious links.
- Update your software when required. Back up important files in case of a data breach so that you can retain details and take appropriate action should a breach occur.
- Review your security policy to stay up to date with company procedures and security protocols.
| Categories | |
| Tags |






